According to the latest WordPress plugin statistics, WooCommerce is tilted as one of the most popular and best WordPress plugins of all time, with over 5 million active installations.
That immense endorsement sometimes comes with a price. That is, this eCommerce titan has become a prime target for attackers.
In particular, WooCommerce reported a critical vulnerability detected on July 2021. This WooCommerce vulnerability did cause a wave of panic among store owners and users.
What is this vulnerability? Did it leave any damage? Has any store been compromised? And what did WooCommerce do to resolve the issue?
Keep reading to find out the answers!
- WooCommerce Vulnerability 2021 Explained
- WooCommerce Vulnerability FAQs
- How to Protect Your WooCommerce Stores from Vulnerabilities
WooCommerce Vulnerability 2021 Explained
On July 12, 2021, a critical WooCommerce vulnerability was spotted related to the WooCommerce and the WooCommerce Blocks plugin. Josh, a security researcher, reported that issue via the HackerOne security program of Automattic.
After carrying out a thorough investigation, WooCommerce detected an SQL injection vulnerability.
As a consequence, any site using WooCommerce or WooCommerce Blocks is strongly recommended to update their plugins if they haven’t already conducted an automatic update.
This WooCommerce vulnerability was so severe that it did affect millions of users. WooCommerce right off the bat rushed out to develop a security patch to fix the problem for each impacted version (90+ releases).
The patch was automatically deployed to vulnerable WooCommerce sites. From a store owner’s perspective, you should make sure both WooCommerce and WooCommerce Blocks are updated to their latest versions (5.5.1).
WooCommerce also advised all site owners to update passwords for admin users. Plus, they suggested rotating API and payment gateway keys used on the store.
So how can you know if your version is up-to-date?
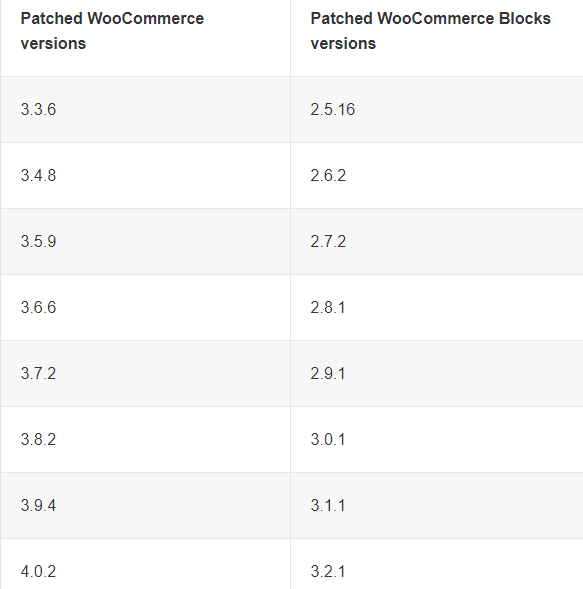
WooCommerce has listed a table of patch versions for both WooCommerce and WooCommerce Blocks.
If you find none of your current versions match any listed version, you should immediately update to the highest available version.
WooCommerce Vulnerability FAQs
#1. What is a WooCommerce SQL Injection Vulnerability?
An SQL Injection allows hackers to interfere with the database using malicious SQL scripts. From here, attackers can gain control over the site. They display information or make the site behave strangely compared to its usual.
Also, according to WordFence, this WooCommerce vulnerability is a Blind SQL Injection vulnerability.
#2. How can I Know If Data was Compromised?
As WooCommerce stated, there is no exact way to confirm whether data was compromised. The team suggests checking the access logs of your webserver to detect some exploit attempts.
This process may take time and need certain coding skills. In case mind touching code, you can seek help from your web host to review your access log.
You can refer to the WooCommerce announcement for more details.
#3. Should Store Owners Alert Their Customers about the Vulnerability?
Notifying customers or not depends on many factors, such as your site infrastructure, what data your site is storing, etc. However, the most crucial thing you should take into account is whether or not your site has been compromised.
Do this first before alerting your customers – update your WooCommerce version to the one with the security patch fixing this issue. This will help protect your clients from any further threats.
Next, keep an eye on your passwords, payment gateways, and WooCommerce API keys. Follow exactly what WooCommerce has recommended:
- Generate new passwords or the Admin on your site, especially if you reuse the same passwords across many sites.
- Rotate WooCommerce and any payment gateway API keys used on your site.
#4. Should I Get the Security Patch Automatically?
No. WooCommerce advises store owners to try manually updating the plugin to the security patched version. There are several reasons for that:
- You’re using an older version of WooCommerce (lower than version 3.3) on your store.
- Automatically updating to the fixed version may cause plugin conflicts.
- You have turned off automatic updates on your store.
- In case your file system is read-only, the automatic update will turn out to be useless.
How to Protect Your WooCommerce Stores from Vulnerabilities
#1. Utilize Security Plugins
Security plugins appear to be the easiest yet effective way to protect your WooCommerce store from vulnerabilities. All you have to do is install them in your store and let them perform the magic.
They will monitor and scan your sites regularly, turn on firewalls, and go overboard to fix security holes on the spot. There are dozens of superb security plugins out there, both free and paid, namely WordFence, Sucuri, JetPack, MalCare, and more.
#2. Back up, Back up, and Back up
Site backup is as essential as any money-making strategy of your business. It proves handy in securing your website from losing all data in case of cyberattacks. Sadly, some WooCommerce merchants have still overlooked it.
To protect your store from unexpected WooCommerce vulnerabilities, you should opt for solid WordPress backup plugins.
Look for the plugin that handles all types of data, such as WordPress files, databases, plugins, and themes. Plus, it should offer flexible backup schedules as well.
#3. Tighten Login Security
We all know that the WordPress login page is always highly targeted for malicious attacks. You need to strengthen login security by
- Limiting login attempts
- Hiding the default login URL
- Avoiding using “admin” as a username
- Making use of Two Factor Authentication (2FA)
#4. Install SECURE Themes and Plugins
Secure themes and plugins refer to the ones coming from authorized and trustworthy sources. These include WordPress plugin repository, theme directory, WooCommerce marketplace, reputed third-party developers, etc.
Aside from that, make sure that you don’t use null WordPress plugins and themes that are innumerably sold at a super low price on the Internet.
Remember, null WordPress themes and plugins suck! They are no other than the container of malware and backdoor to attack.
We can’t stress enough how much secure themes and plugins mean to site security. Check out our WordPress security statistics to know the reason why.
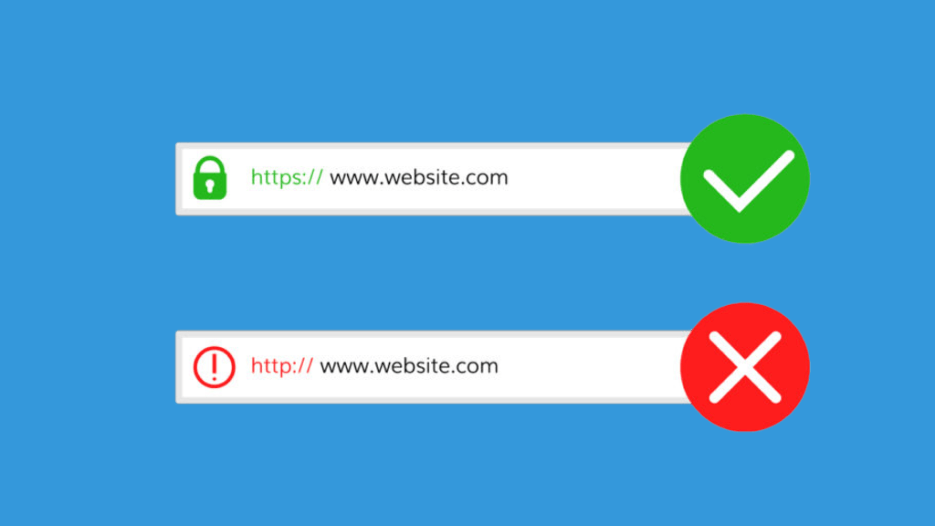
#5. Install an SSL Certificate
Does your site get an SSL certificate? If yes, congratulation, you have added an extra security layer to your store. All confidential data of you and your customers are secure.
An SSL certificate will ensure that the data exchanged between your customers and the store will be encrypted. At that point, all confidential data of your customers, including bank details, transactions between you both, etc. are secure.
In case your answer falls to “Not yet,” you need to get an SSL certificate for your store asap! Why? Because Google has included SSL as one of the ranking factors.
#6. Regularly Update Your Site
Most site owners tend to forget or hate updating their sites as they worry the new version will cause conflicts. That’s a really bad habit.
Apart from that, just updating WordPress and WooCommerce is not enough. You have to make sure all plugins on your site are up-to-date. Remove unused or any plugin that hasn’t been tested with the latest versions of WordPress as well.
Pro-tip: Try to make an updating schedule and maintain it so that you won’t miss out on it.
Is WooCommerce still Safe?
Yes, definitely!
According to WordFence Threat Intelligence, there is extremely little evidence of compromised stores. So you should be confident that there is no widespread attack harming WooCommerce sites and WooCommerce is still safe and powerful.
This article has spelled out what WooCommerce vulnerability is, how it affected site owners and how WooCommerce responded to the issue.
On top of that, we’ve also shown you best practices to safeguard your WooCommerce stores from vulnerabilities.
Do you have any comments on this WooCommerce vulnerability? Share your thoughts in the comment section below!
 (
(